Hiring a Virtual Chief Information Security Officer (vCISO) on a part-time or as-needed basis helps organizations gain security expertise without the overhead costs of a full-time hire. The decision between a vCISO and a traditional in-house CISO depends on the...
Celebrating the Successes of the Packet Hacking Village at DEF CON 31 The Packet Hacking Village at DEF CON 31 sponsored by Aries Security was a massive success all around. This was a place where cybersecurity professionals and enthusiasts could flex their skills and...
Hardwired Competition at DEF CON: Building a Network Cable Against the Clock DEF CON, the famous annual hacking conference held in Las Vegas, is known for its intense competitions and challenges that test the skills of the best hackers in the world. One such...
 A Recap of Capture The Packet at DEF CON Every year, the Packet Hacking Village at DEF CON attracts attendees from various corners of the world, with a keen interest in cybersecurity. This year, Aries Security, a primary sponsor of the village, once again presented...
A Recap of Capture The Packet at DEF CON Every year, the Packet Hacking Village at DEF CON attracts attendees from various corners of the world, with a keen interest in cybersecurity. This year, Aries Security, a primary sponsor of the village, once again presented...
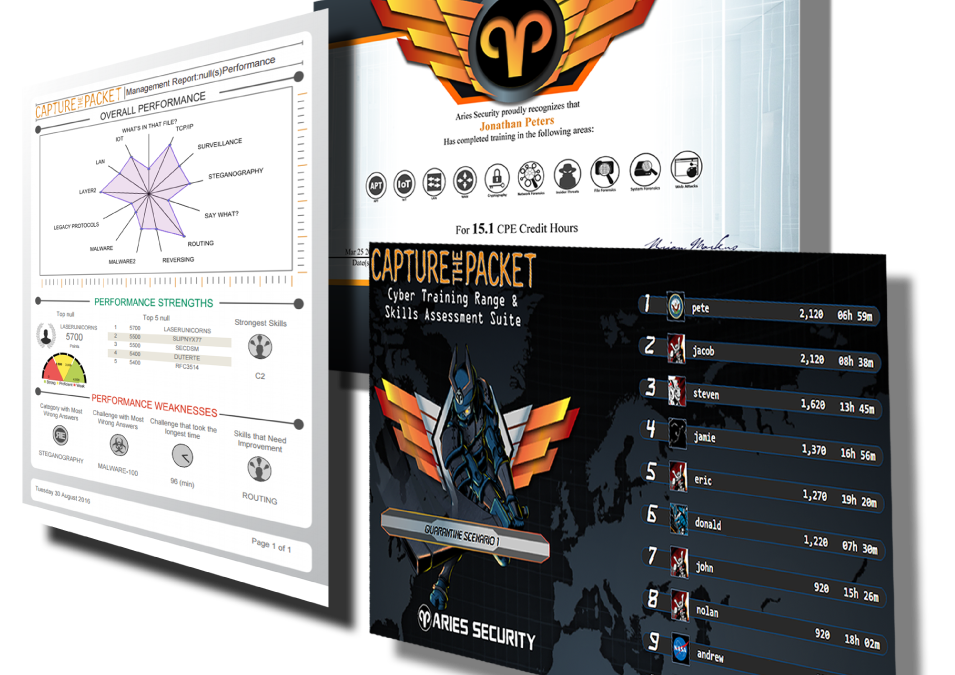 Aries Security Wins Contract With Pikes Peak State College Aries Security has recently been awarded a contract with Pikes Peak State College of Colorado to provide them with their 6th generation Capture The Packet system. This is great news for both Aries Security and...
Aries Security Wins Contract With Pikes Peak State College Aries Security has recently been awarded a contract with Pikes Peak State College of Colorado to provide them with their 6th generation Capture The Packet system. This is great news for both Aries Security and...
 What Bug Bounties Are and How They Work When a company releases a new product or updates its system, they often run into bugs or errors that need to be fixed. These bugs are usually discovered by their development team, but what happens if the team can’t find...
What Bug Bounties Are and How They Work When a company releases a new product or updates its system, they often run into bugs or errors that need to be fixed. These bugs are usually discovered by their development team, but what happens if the team can’t find...



Recent Comments